Phoenix Technical Services & Sales Division
Dr. Michael Lavine, Phoenix Chief Technology Officer

You see it on the news almost weekly! Corporations, Governments, and the News Media constantly are targeted by hostile governments and opposition parties, criminal organizations, hackers, and disgruntled employees ("Insider Threats"). Critical technology infrastructure, military bases, public buildings, sport stadiums, power stations, offshore oil & gas platforms and political leaders are all vulnerable to drone attacks. These threats are real and should not be under-estimated.
Our Mission is to ensure the security and authorized access to our Clients' entities, to meet these challenges PHOENIX Group - introduces the Phoenix Technical Services & Sales Division and through or partners CTL Systemware and department 13 Counter Drone System we are in a unique position to mitigate hostile Ransomware & Hacking activities and protect from drone attacks.
Dr. Michael Lavine, Phoenix Chief Technology Officer, will head the new division and brings with him knowledge and experience in these areas to address our clients specific needs.
- PhD in Management Information Systems, Critical Infrastructure Protection, from Cass Business School, City University of London.
- MSc from Johns Hopkins University & City University of London.
- Assistant Professor/Lecturer at JHU’s Whiting School of Engineering, Department of Computer Sciences & the JHU Information Security Institute.
- Past Director, JHU Computer Forensics Laboratory.
- Full Adjunct Professor at University of Maryland, School of Cybersecurity and Information Technology.
- Lead SME in development of two online M.S. Degrees Programs in Cybersecurity and Information Assurance.
- SME Advisor and Training Consultant to US Department of Defense, US Department of the Treasury, US House of Representatives, Bank of America, Bank of China, Microsoft, and ISO Working Group.
Phoenix Technical Services - Mission
Phoenix Technical Services - is focused on "Multi-phase Cyber Security Assessment, Audit, and Upgrade" - "Ransomware & Hacking" - "Counter Drone Mitigation"

A question of "WHEN" and not "IF" !





Ransomware & Hacking Costs
Considerations
- What will be the operational and financial impact for company operations, the financial losses, the disruption of the supply chain to your Clients???
- What would be the damage to the international reputation and brand recognition??
- How will the company recover from and mitigate future attacks???
Conduct a Multi-phase Cyber Security Assessment, Audit, and Upgrade
Phase I: Business Impact Analysis and Vulnerability Assessment
- "Road map" all IT systems (network, email, web, wireless, business information systems, banking, payments, etc).
- Establish the profiles of internal and external actors that may pose a threat and how currently managed.
- Identify the vulnerabilities of all information systems, how they could be exploited, and opportunities for enhancement.
- Evaluate the effectiveness of current IT security measures.
- Deliver Report on vulnerabilities, shortcomings in IT security, and recommendations for the current security program.

Phase II: Advanced Persistent Threat Analysis and Network Security Audit
- Model behavior of malicious viruses, worms, botnets, trojans, ransomware, spearfishing, phishing, and other current adverse technologies through deep scanning and evaluation of security protocols, procedures, and internal audits.
- Conduct comprehensive Security Audit of the Corporate network, to include virtual private networks, extranet, wireless, and all main components.
- Perform External Penetration Test (“White Hackers” at off-site labs) to determine if access of most sensitive components can be executed without detection.
- Conduct Internal Penetration Test (“White Hackers” working from within Corporate network) to determine if access to non-authorized areas can be executed without detection.
- Delivery Reports on all Findings and Recommendations for enhancements.

Phase III: Review of Cyber Security Policies, Procedures, & Training
- Evaluation and review of Active Network Defense (Incident Response and Management), Intrusion Prevention and Detection procedures, Highly Privilege Account Access, Firewall Appliance, high risk remediations, etc.
- Review of Business Continuity Plan and Disaster Preparedness Policies and Plans.
- Review the implementation of recommendations from past “Exercises” and, if relevant prepare and lead an Exercise of a simulated cyber hacking/attack and the implementation of the current mitigation plans and procedures.
- Evaluate current Cyber Security Awareness training program for employees. As relevant, develop customized employee training courses based on job position/function and level of access to IT systems. Train-the-trainer or Phoenix experts can conduct the training in-person and/or via dedicated web education platform.
- Delivery Reports on all Findings and Recommendations of the Reviews performed, Lessons Learned from the Exercise, and Employee training.

Phoenix and CTL|SystemWare Spectrum Guard Hacking and Ransomware Solution


A question of "WHEN" and not "IF" !




What is the Threat
With sales of drones around the world exceeding $14 billion in 2015, and growing by 60% in 2016, the threat posed by the weaponization of recreational drones already is a reality. The unregulated proliferation of drones in most countries poses a significant danger to their national security.
Phoenix | department 13 MESMER® Drone Mitigation Solution
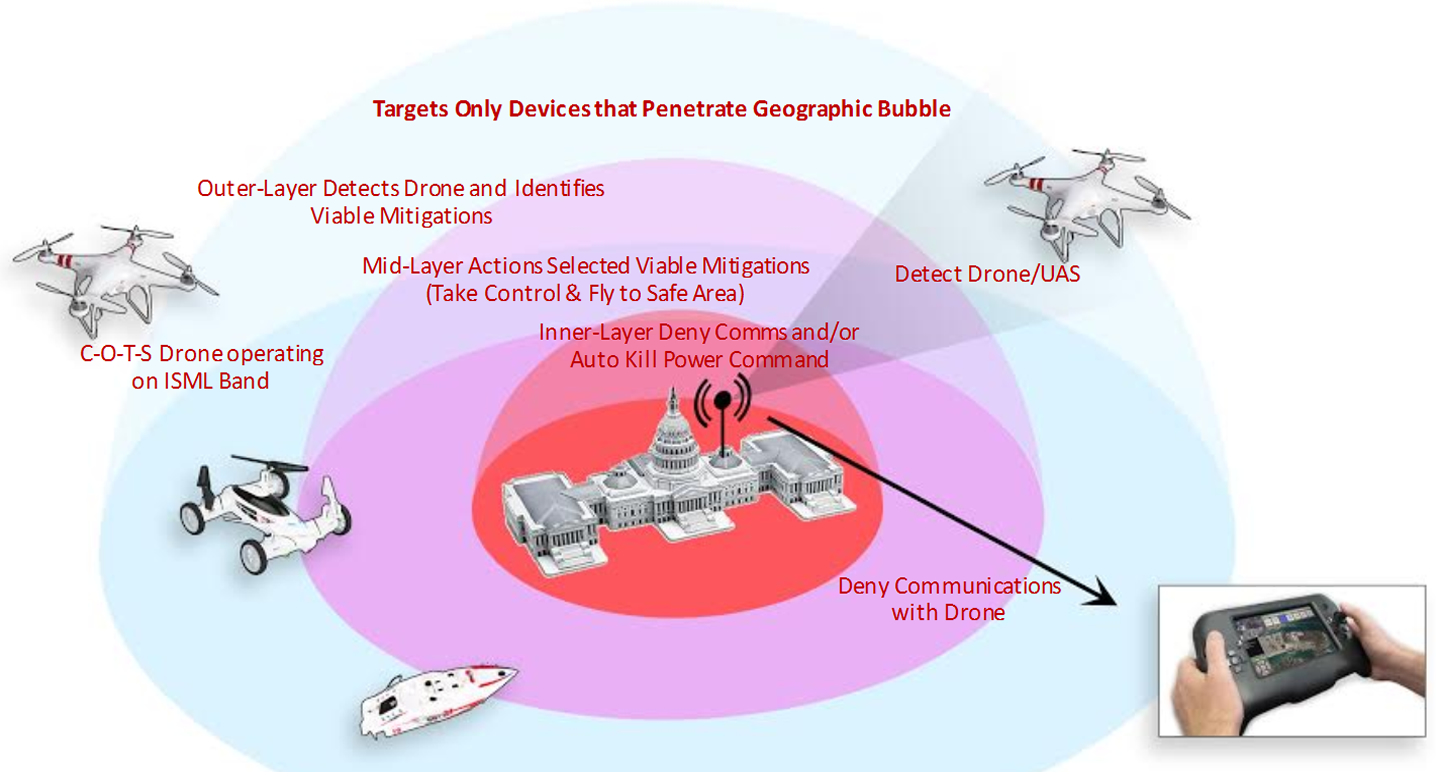
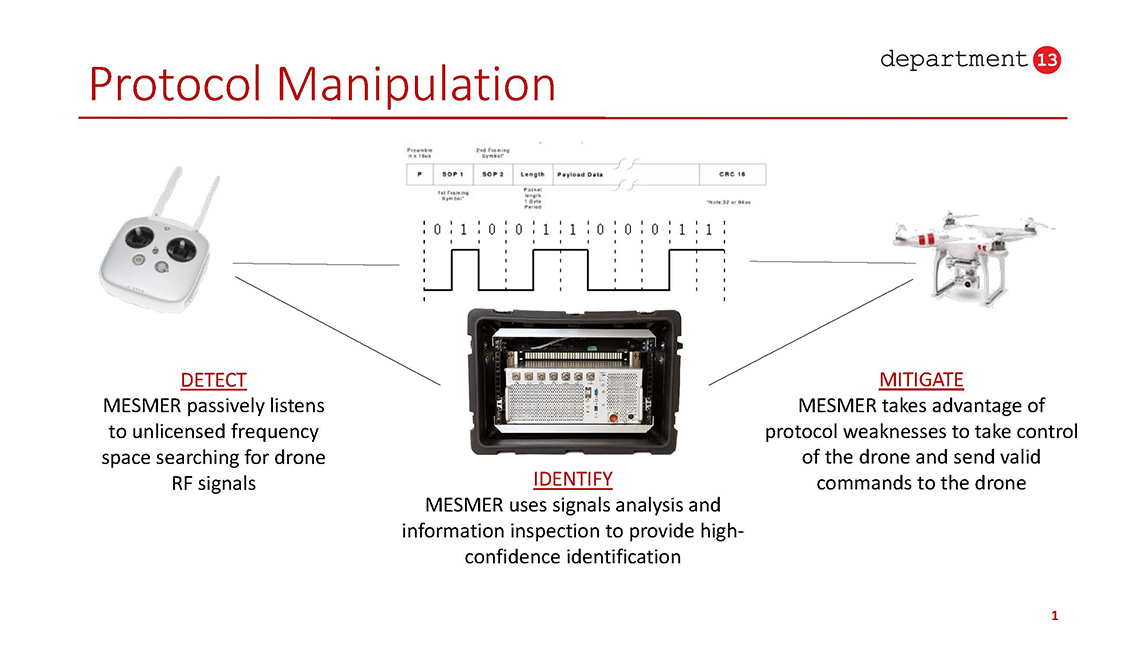
Protocol Manipulation
Mitigation Options

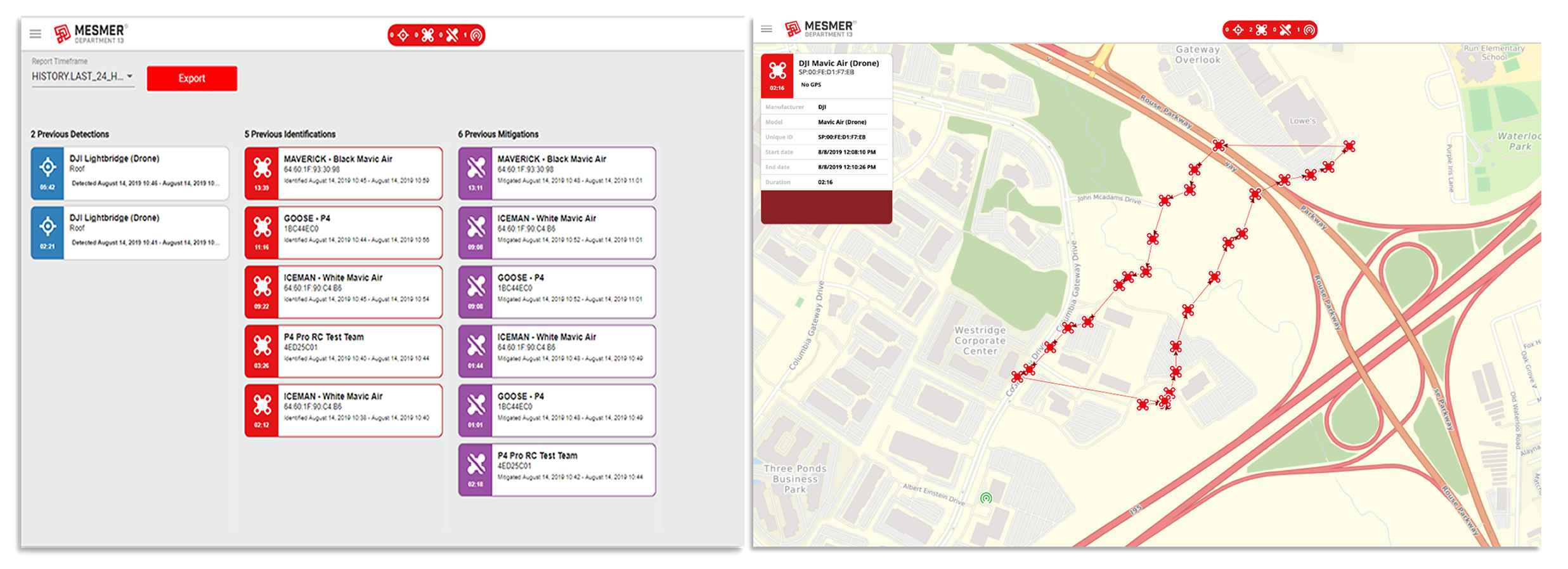
department 13 MESMER® User Interface
User Interface Utilizes the ATAK Application / Web Browser for Integration Flexibility
- Displays drones detected within the protected area by model.
- Displays drones that are “blacklisted” (known enemy drones) and “whitelisted” (known friendly drones).
- Mitigation options (dependent on drone type) and execution status, i.e.
- Land in safe zone
- Land in place
- Return to Launch Point
- Auto-mitigation mode: automatically mitigates to a predetermined default mitigation reducing drone mitigation time Mapping (drone dependent)
- Telemetry data (drone dependent)
- Detection history: log of drone type and when the drone was detected for intel analysis

department 13 MESMER® Drone Locating
department 13 MESMER® System Description

Phoenix | department 13 MESMER® Counter Drone Solution





